How a misconfigured Lotus Domino Server can lead to Disclosure of PII Data of Employees, Configuration Details about the Active Directory, etc | by Aayush Vishnoi | Medium

How a misconfigured Lotus Domino Server can lead to Disclosure of PII Data of Employees, Configuration Details about the Active Directory, etc | by Aayush Vishnoi | Medium

Ibm Lotus Domino Designer 6 Application Development With Lotus Domino Designer | PDF | Ibm Notes | Databases

Solved: Trellix Support Community - ENS Exploit Prevention - "Suspicious Double File E... - Support Community
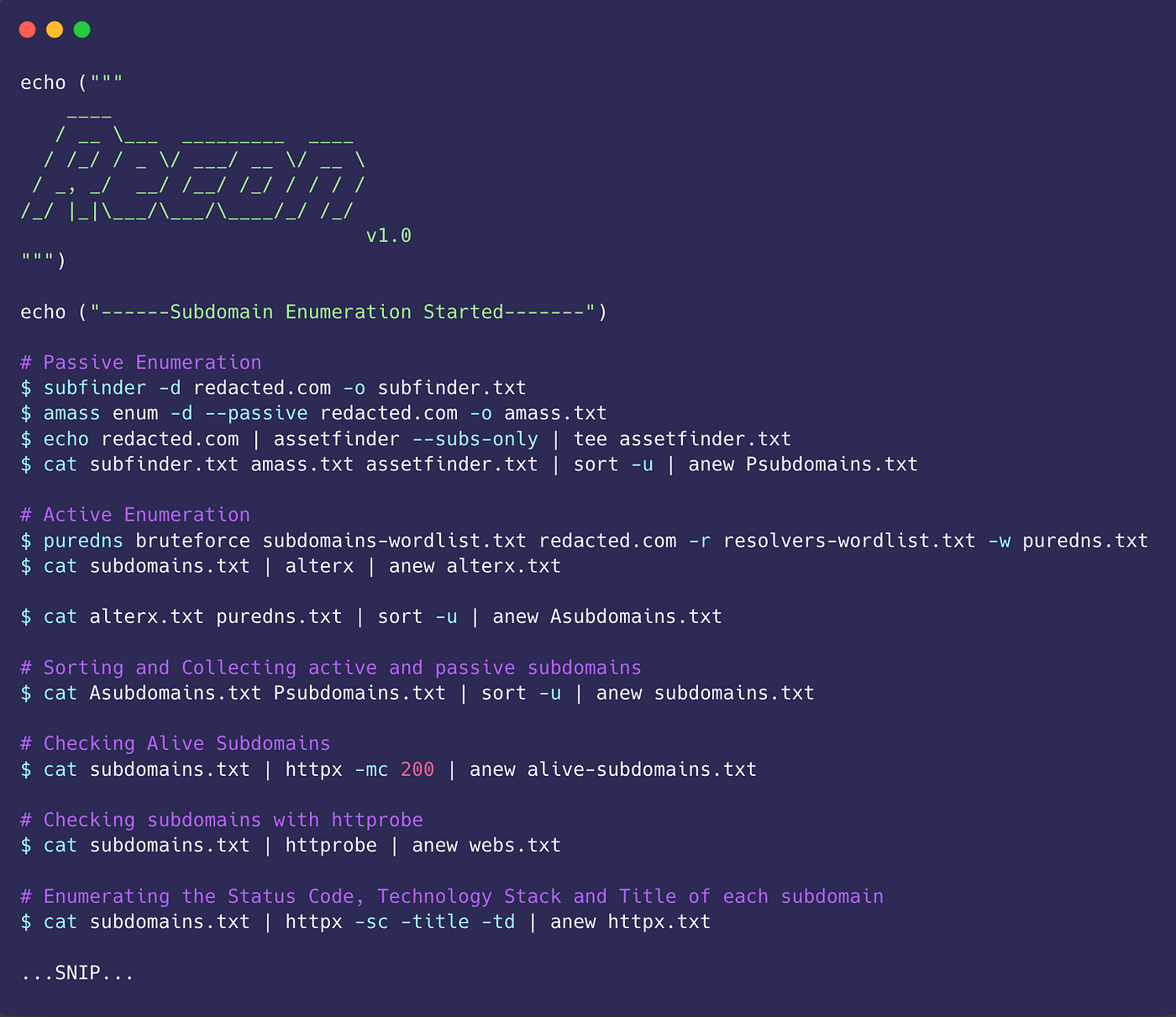
How a misconfigured Lotus Domino Server can lead to Disclosure of PII Data of Employees, Configuration Details about the Active Directory, etc | by Aayush Vishnoi | Medium
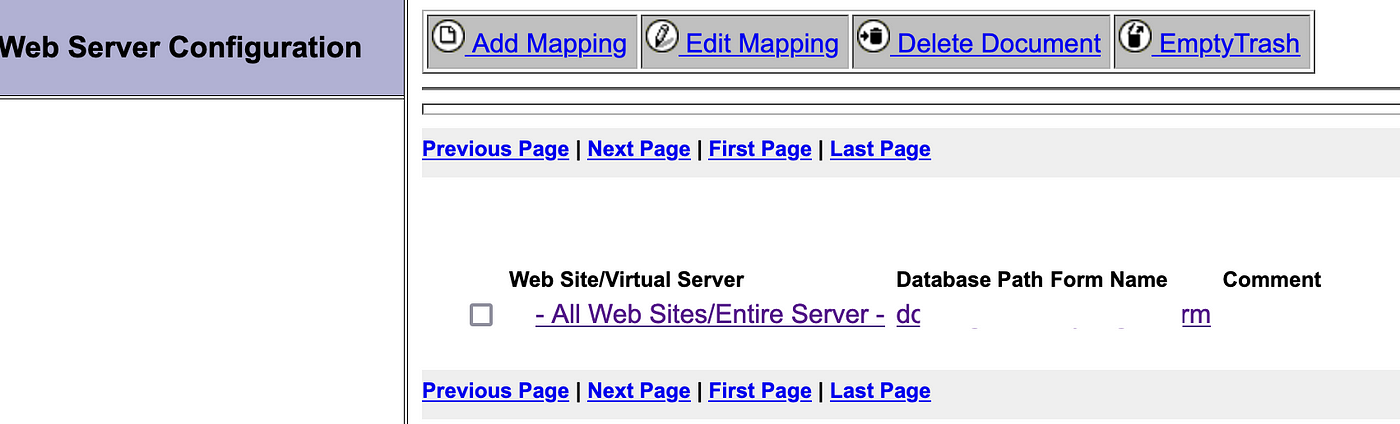
How a misconfigured Lotus Domino Server can lead to Disclosure of PII Data of Employees, Configuration Details about the Active Directory, etc | by Aayush Vishnoi | Medium

Make sure that the “Names.nsf” cannot be accessed via Internet! – Thoughts about HCL Connections, Domino and Sametime